In IT security circles, Emotet is one of the most notorious and prominent examples of malware in recent years. If you don't know about Emotet then it is even more important that you learn what Emotet is and how to protect yourself against it - because that could be one of the best things you will ever do.
What is Emotet?
Emotet is a special type of malware created by cyber criminals. This malware was first
discovered in 2014 during a cyber attack on banks in Germany and Austria. Emotet
gained worldwide attention in the late 2010s thanks to several successful,
high-profile attacks.
Emotet is an
unusual type of malware in that it is constantly evolving and staying active. Usually,
when malware is identified and technology is developed to block it, cyber
criminals create a new type of malware that is then renamed.
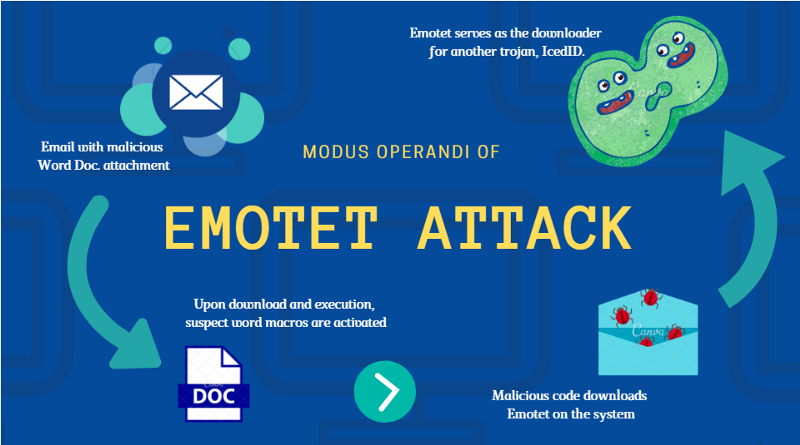
Cyber
criminals typically spread Emotet malware via spam email. A typical way
to target users is to send a document with a standard title, such as: B.
"Invoice.doc" so that the attachment is considered legitimate by many
users when they receive it. As soon as the recipient opens the attachment,
Emotet uses macros within the document to download itself to their system and
get to work.
Many Emotet
emails also contain malicious links with frequently-clicked terms such as
“payment details” in their content.
Many Emotet
attacks make it appear that the email you receive is from a well-known brand. This
has helped the number of successful attacks to increase over the years.
Other
factors that make this type of malware so dangerous are that it can lodge
itself on systems and operate undetected, bringing various types of malware
onto your system in the process. Once you identify and remove Emotet from
your system, you may still need to do more work to remove additional malware.
How has Emotet developed in recent years?
To this day,
Emotet malware continues to evolve and has far more capabilities than in 2014.
- The first version of
Emotet was created to intercept internet traffic with the aim of stealing
banking information.
- The second version in
2014 included modules that automatically targeted German and Austrian
banks. It also included a referral system so the fraud could be
carried out quickly before security systems sounded the alarm.
- A 2015 update
included additional camouflage capabilities that hid Emotet from most
antivirus programs. It also began to target banks in Switzerland ...
These early
versions of Emotet were Trojan horses designed primarily to steal
banking information and conduct illegal money transfers.
2018 and beyond
In 2018 Emotet evolved
from a traditional Trojan malware to a so-called "dropper". This
means that Emotet can not only infect systems, but also transfer and download
other Trojan horses and ransomware onto computer systems. As a result, an
Emotet attack can result in both data being stolen without knowledge and an
individual, company or other organization falling victim to ransomware. It
is believed that this happens via the creators of Emotet, who "rent"
their software to other criminals. The criminals pay for the malware so
that they can access data and keep 100% of the profits from their ransomware or
other malware.
In 2019 , Emotet was used
as a botnet to attack a large number of people and organizations, especially
banks from Europe and the USA.
Emotet is
still active in 2021 ,
with campaigns discovered throughout the year. At the end of 2020, it was
found that the malware was spreading from around 50,000 parked domains. These
parked domains are newly registered and immediately parked domains or existing
good standing domains that the previous owner did not renew.
Five famous malware attacks with Emotet
Emotet has
been the cause of several high profile cyberattacks in recent years. Five
of the most important are:
- An
attack was carried out on the Allentown, Pennsylvania local government in
February 2018 that infiltrated the
local government computer systems. While nothing was spent on
ransomware payouts, the total cost to fix and mitigate the damage caused
by the attack was more than $ 1 million.
- An
attack on the city of Lake City, Florida in July 2019 caused $ 460,000 in damage due to
ransomware payouts .
- In
May 2019 there was an attack on the Heise Group ,
a publishing house based in Germany. This attack was caused by an
employee opening what appeared to be a legitimate email attachment. However,
it is not known what, if any, financial damage occurred.
- In
August 2020, there was an attack on the Quebec Justice Department in Canada . Although
the Justice Department said no data was stolen or financial damage was
incurred, the Department has been heavily criticized for its slow response
to the problem. In December 2020, the ministry continues to be
accused of not correctly assessing the severity of the attack.
- Throughout
September 2020, government agencies across Europe reported increased
Emotet activity and attempted fraud. However, it is not known to what
extent these were successful.
How does Emotet malware spread and why is it so difficult
to detect?
Emotet
typically spreads through email systems by hijacking accounts and sending
malicious emails.
Once in your
system, the malware will search your inbox and email contact list. It can
then reply to real email messages with malicious attachments or links. This
is another factor that makes Emotet more dangerous than traditional phishing
scam emails, which are often easy to spot as they are randomly sent from an
unknown source.
Since the
people on your contact list will receive an email that looks like a real reply
- to an email they actually sent - they are more likely to open it and click
the attachment or link. If they do, the malware can infect their system,
steal data, install other malware, and repeat the process with that person's
email account.
Detecting
Emotet is difficult because it is programmed to bypass most antivirus products. A
traditional virus uses the same code “signature” every time it tries to
establish itself on your system. So as long as your antivirus software
knows what signature to look for, it can block these viruses.
In contrast,
Emotet is a so-called polymorphic virus. This means that the malware's
“signature” changes on every computer it installs on, and the anti-virus
software cannot detect it. Emotet also detects when it is running in a
virtual machine and can automate itself to rest until it can act effectively.
How can you protect yourself from Emotet?
The most
effective means of protection against this malware is finding a SIEM solution
that can help identify and help quarantine Emotet emails and those containing associated malware such as Ryuk ransomware . A
SIEM solution such as LogPoint, can help detect Emotet and bring an added layer
of security to your business emails.
The most
effective protection against this malware is a SIEM solution that can help identify
and quarantine Emotet emails and those containing related malware such as
Ryuk Ransomware . A SIEM solution like LogPoint can help
identify Emotet and create an additional layer of security for your business
emails.
In addition
to choosing software that will help you block Emotet attacks and continuously
monitor your internal networks, you should also:
- Disable the use of
macros in Microsoft Office files.
- Install total security software and updates as soon as they are available for the software you are using.
- Make regular backup copies of all data and keep them safe in a separate location from the master files.
- Create a culture of
care in your company. If employees are careful which attachments they
open - or you use cloud software to make attachments meaningless - you
minimize your risk of falling victim to Emotet to almost zero. Make
sure your team doesn't take the use of security software as a false sense
of security!
What actions can you take if your systems are affected by
Emotet?
If you think
you may have an Emotet infection, do the following:
- Remove potentially
infected systems from your network.
- Check the system and
remove the malware if you can confirm it is there. It may be
necessary to erase and reinstall the system.
- Look for other
ransomware and other malware that Emotet may have dropped. If these
are present, you should remove them as well.
- Check and clean every
other system on your network, one at a time. Remember that Emotet can
rest on your systems. You need to invest the time to make sure you
don't run into a problem right away, even though you feel you have
eliminated it.
- Once you have confirmed
that the malware is not present on your network, reintegrate the system on
which you identified the original infection.
Comments
Post a Comment